Original source publication: de Sá-Soares, F., D. Soares and J. Arnaud (2014). A Catalog of Information Systems Outsourcing Risks. International Journal of Information Systems and Project Management 2(3), 23–43.
The final publication is available here.
A Catalog of Information Systems Outsourcing Risks
Departament of Information Systems and Center ALGORITMI, University of Minho, Guimarães, Portugal
Abstract
Information systems outsourcing risks are a vital component in the decision and management process associated to the provision of information systems and technology services by a provider to a customer. Although there is a rich literature on information systems outsourcing risks, the accumulated knowledge on this area is fragmented. In view of this situation, an argument is put forward on the usefulness of having a theory that integrates the various constructs related to information systems outsourcing risks. This study aims to contribute towards the synthesis of that theory, by proposing a conceptual framework for interpreting the literature and presenting a catalog of information systems outsourcing risks. The conceptual framework articulates together six key risk elements, namely dangers, negative outcomes, undesirable consequences, factors and mitigation actions. The catalog condenses and categorizes the information systems outsourcing risk elements found on the literature reviewed, both from the perspective of the outsourcing customer and from the perspective of the outsourcing provider. Proposals for subsequent work towards the generation of the theory of information systems outsourcing risk are suggested.
Keywords: Information Systems Outsourcing; Risk; Theory
1. Introduction
The survivability and prosperity of any organization depends crucially on its capability to perform a set of activities that result in the delivery of a valuable product or service for the market. In order to enhance their value chain, organizations use various technological and managerial solutions to support their business processes. These solutions may be developed internally or procured externally to the organization, configuring the two main ways to obtain any type of resources—insourcing and outsourcing. Confronted with fierce competition in the context of global economic and financial crises, companies strive for greater efficiency and reduced costs, while at the same time try to increase their specialization in a limited number of key areas. This state of affairs may tip organizations to the outsourcing side of the sourcing binomial, transforming the outsourcing option in a critical strategic decision [McIvor 2008].
In the realm of information systems (IS), outsourcing involves making arrangements with an external party for the partial or total provision of the management and operation of an organization’s information technology (IT) assets or activities [Kern and Willcocks 2001]. These arrangements take the form of contracts that state the agreement between two entities: the customer of the outsourcing services and the provider (or providers) of those services.
The relevance of IS outsourcing is evidenced by Gartner’s forecasts of a worldwide market reaching $288 billion in 2013 [Gartner 2013] and of a growth rate of 5.2% in 2014 [Gartner 2014]. It may also be appreciated by considering the accumulated knowledge produced on the area (cf. [Dibbern et al. 2004] and [Lacity et al. 2009]).
Prior to embark upon an IS outsourcing project, an organization should ponder the expected costs and benefits of the outsourcing option. If the organization decides to proceed with the outsourcing, the consideration of the cost-benefit relationship should persist, in order to take into account the benefits really achieved and the costs incurred. Similarly, an outsourcing provider needs to consider the costs and benefits of starting an outsourcing transaction with a potential customer, as well as to track the evolution of the costs and benefits of an ongoing outsourcing contract. Associated with benefits and costs of an outsourcing deal there is a set of risks. These risks need to be managed if the transaction between an outsourcing customer and one or more outsourcing providers is to be successful.
Various studies have been conducted on IS outsourcing risks, addressing issues such as sources of risks, profiling and prioritization of risks, and actions to reduce the impact of risks. To some extent, that collection of works forms a fragmented, although extremely valuable, set of contributions. This interpretation motivated us to seek an integrated view of IS outsourcing risks. In fact, some authors have already made efforts to that end, such as Bahli and Rivard [Bahli and Rivard 2003] who extended the risk assessment framework used in engineering to analyze IS outsourcing risks, suggesting the need to combine risk scenarios, risk factors, consequences and mitigation mechanisms. This paper builds upon that collection of studies and integrative efforts. Our goal is to contribute towards the synthesis of a theory of IS outsourcing risk by compiling a catalog of IS outsourcing risks. We believe that a theory of IS outsourcing risk may prove particularly useful to practitioners analyzing the feasibility of an IS outsourcing project or steering ongoing IS outsourcing transactions and to researchers deepening our understanding of the IS outsourcing risk management process.
The paper is structured as follows. After this introduction, a conceptual framework for interpreting the literature on IS outsourcing risks is proposed, followed by the description of the work undertook. Next, the catalog of IS outsourcing risks derived from the classification of the literature is presented and discussed. Finally, conclusions are drawn, limitations of the study are acknowledged and future work is suggested.
2. Conceptual Framework
The aim of this study is to make a contribution in the domain of IS outsourcing that may assist in the near future in the creation of a theory of IS outsourcing risk. As formulated, this ultimate objective builds on three main concepts: IS outsourcing, theory and risk. As a first step towards that research goal, we will briefly discuss each of these three concepts in order to develop a conceptual framework on which to base the generation of such theory.
Information systems outsourcing is not a new phenomenon. Since its emergence in the 1960s, it has undergone several changes: from an emphasis on time-sharing services, it evolved to the application service provision (ASP) model in the late 90s, and then to service-oriented computing (SOC) and on-demand/utility computing in the beginning of this century [Vassiliadis et al. 2006]. Also, from a geographical point of view, it has diversified from domestic provision of services by third parties to offshore outsourcing, where the responsibility for management and delivery of IT services is located in a different country from that of the customer [Sabherwal 1999].
The literature on IS outsourcing is significant and diverse. Lacity et al. [2009] classified 191 papers on IS outsourcing published between 1990 and 2008 into six topics relevant to practice. The set of topics and the associated questions
addressed by researchers are the following:
Determinants of IS outsourcing—Which types of firms are more likely to outsource IS?
IS outsourcing strategy—What is the strategic intent behind IS outsourcing decisions? What are the strategic effects of IS outsourcing decisions?
IS outsourcing risks—What are the risks of IS outsourcing? How are IS outsourcing risks mitigated?
Determinants of IS outsourcing success—Which practices increase the likelihood that a customer’s outsourcing decision will be successful?
Customer and provider capabilities—Which capabilities do customer firms need to develop to successfully engage IS outsourcing providers? Which capabilities do customer firms seek in an IS outsourcing provider?
Sourcing varietals—How do practices differ when pursuing different types of outsourcing such as offshore outsourcing, application service provision, and business process outsourcing?
The second fundamental concept we review is theory. A theory is a set of defined and interrelated constructs that presents a systematic view of phenomena [Kerlinger 1986]. In order to be considered a theory, a conceptual artifact must identify the constructs that compose it, specify the relationships among these constructs, and be formulated so that these relationships are able to be tested, i.e., are falsifiable [Doty and Glick 1994].
The importance of theory may be appreciated by considering its primary goals: analysis and description (description of the phenomenon of interest and analysis of the relationships among constructs), explanation (how, why, and when things happen), prediction (what will happen if certain preconditions hold) and prescription (provision of a recipe to the construction of an artifact) [Gregor 2006]. In this study we are interested in the IS outsourcing phenomenon from the perspective of risk, our third fundamental concept to discuss.
Despite the diversity of meanings of the term risk, Renn [1992] isolated a common element among all definitions, namely the distinction between reality and possibility. Under this assumption, that author defined risk as the possibility that human actions or events lead to consequences that have an impact on what people value [Renn 1992]. In a similar vein, the standard ISO 31000 defines risk as the effect (positive and/or negative) of uncertainty on objectives [ISO 2009]. At this point a distinction between risk and uncertainty is needed. As soon as 1921, Knight contrasted between the concepts of uncertainty and risk, noting that the former is present when the likelihood of future events is indefinite or incalculable, while the latter is present when future events occur with measurable probability [Knight 1921]. This distinction contributes to correctly place the role of likelihood (probability) in risk related constructs. A final important derivation from the conception of risk by Renn [1992] is that risks may be conceived as mental representations of threats capable of causing losses or as opportunities that can produce gains. This last alternative view of the concept of risk is in sharp contrast with the common view that associates risk to hazard. In this study we adopted the former view of risk, focusing our attention on the possibility of some unfavorable event or outcome occur in the realm of IS outsourcing. Nevertheless, we will address the usefulness of the alternative view of risk for the management of IS outsourcing in the conclusion section of this paper.
Given the aim of this study, the review of literature on the concepts of theory and risk prompted us to develop a conceptual framework that could provide a basis for constructing a theory of IS outsourcing risk, by shaping and organizing our interpretation of the findings in IS outsourcing literature. To this end, we propose the conceptual framework illustrated in Figure 1.
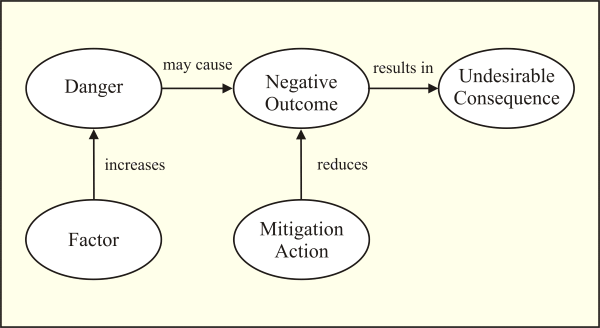
Figure 1: Conceptual Framework
A danger is a potential cause of a negative outcome; it is not, by itself, a realized damage. A negative outcome is an adverse result from which derives an undesirable consequence. An undesirable consequence configures an explicit loss to the entity (in this case the organization), in terms of tangible or intangible assets or opportunities to reap future benefits. Both dangers and negative outcomes are possibilities that may culminate in undesirable consequences. A negative outcome and the originating danger are of interest to an organization due to the undesirable consequences that may entail for the organization. Associated with a danger and a negative outcome there is a likelihood of occurrence. Different dangers and negative outcomes may present distinct levels of severity. In contrast, a factor is an attribute of some entity or situation that increases the exposure of the organization to a danger. Contrary to dangers and negative outcomes, at a given time a factor has a well determined non-probabilistic value. Finally, a mitigation action consists in an act, usually performed by the entity that may suffer the undesirable consequence, expected to lessen the intensity of a negative outcome, eventually nullifying it.
3. Study Description
The nature of the risk elements was also considered by identifying for each undesirable consequence the corresponding type of loss and for each negative outcome, danger, factor and mitigation action their respective foci, i.e., the target object of the element. For each negative outcome and factor we also determined their loci—for the negative outcomes according to the emphasis of the risk element, and for the factors if they concerned the customer (Cust), the provider (Prov) or the transaction (Tran) that takes place between those two parties. The identification of the foci and the determination of the loci was an inductive process, a la grounded theory, where categories were formed based on the concepts covered in each of the risk elements. From this classification and characterization process resulted an artifact in the form of a catalog of IS outsourcing risks which is presented in the next section. The catalog is organized in two parts, accordingly to the perspective of the outsourcing customer and from the perspective of the outsourcing provider. For each party, the risk elements composing the conceptual framework—undesirable consequences, negative outcomes, dangers, factors, and mitigation actions—are listed and discussed.
4. Catalog of Information Systems Outsourcing Risks
4.1 Customer Side View
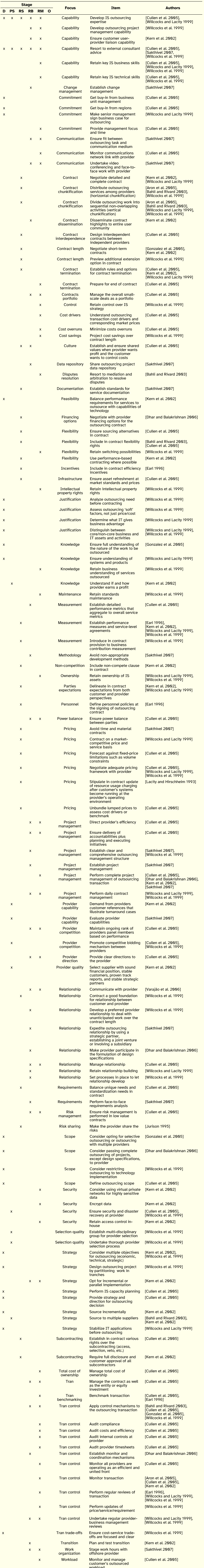
The undesirable consequences for the IS outsourcing customer condensed from literature are shown in Table 1. Of the 17 issues, the loss of critical skills and competences by the customer on the domain of the services outsourced is the most referenced (14 authors), followed by unexpected transition costs of IS services and loss of control over IS decisions. The type of loss most often cited is financial, usually expressing situations where the customer incurs additional costs not expected or not anticipated. The group of undesirable consequences concentrates on the execution phase of the contract and on the post-contract phase. This set of issues suggests that practitioners may find useful to consider the overall risk of an outsourcing transaction according to six types of potential losses, namely in terms of capability and internal control, image and morale, and strategy and finance.
Table 1: Customer-side Undesirable Consequences
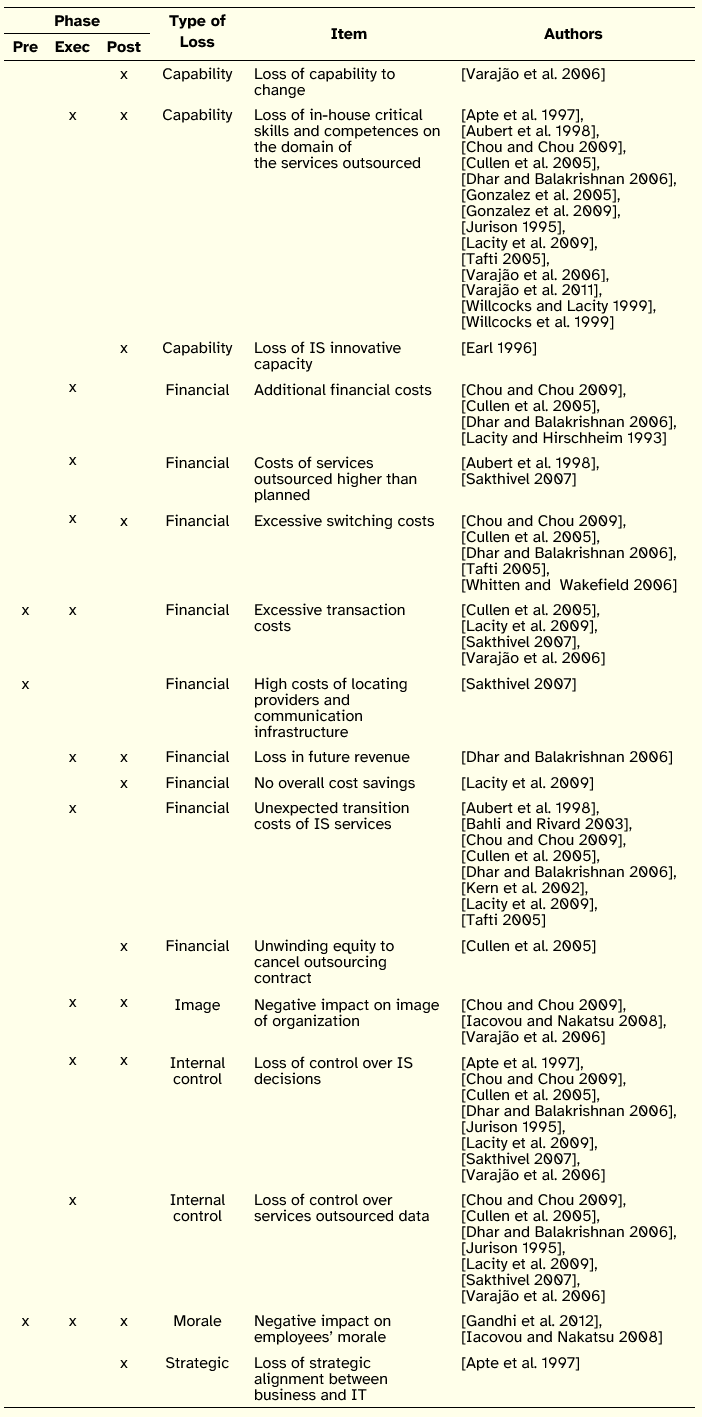
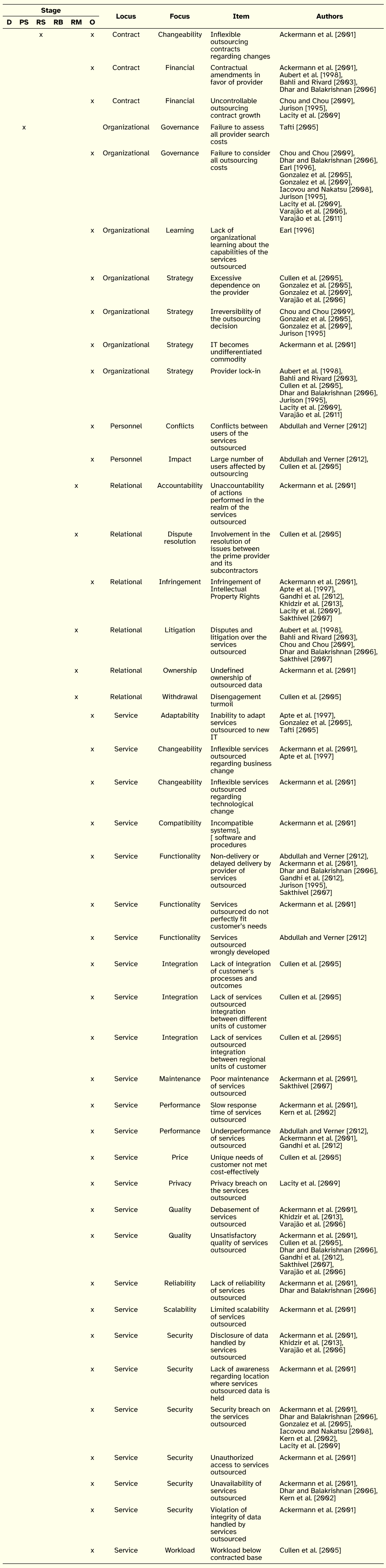
Table 2 groups the issues classified as negative outcomes. The most reported negative outcome relates to the general nature of the previous discussed financial undesirable consequences, namely the failure by the customer team responsible for the governance of the transaction to consider all the costs associated with the provision of IS outsourcing services. Of all 44 issues, 59% were classified in the Service category, with the outcomes regarding non-delivery or delayed delivery of services, unsatisfactory quality of services and security breaches in services concentrating the largest number of references. The second most represented category is Organizational, which includes the second most cited negative outcome, namely Provider lock-in. As it might be expected, the outsourcing stage that by far brings together more aspects is Outcomes (38 in 44). The stages Decision and Relationship Building have no issues, suggesting the need for more research on the adverse results that an organization may face during the crucial periods of deciding on outsourcing and laying the foundations for a smooth relationship with the provider.
Table 2: Customer-side Negative Outcomes
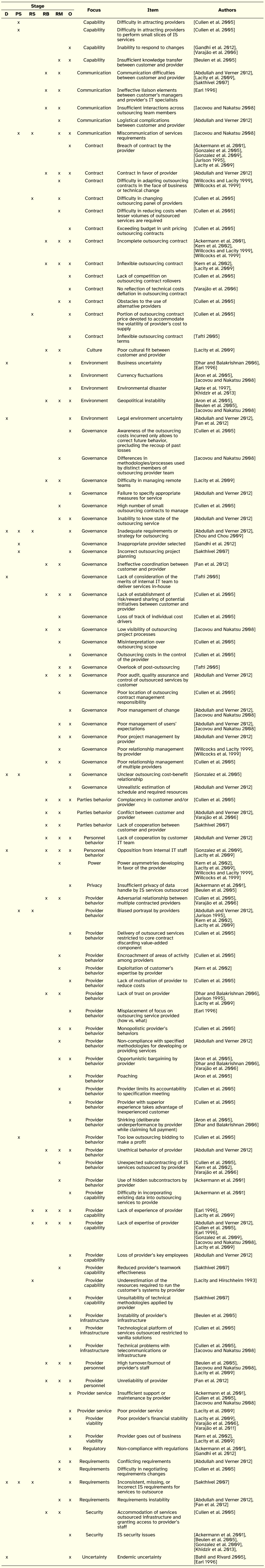
The construct with the second largest number of issues is Danger, with a total of 104, as depicted in Table 3. Although the range of issues is very broad, three foci stand out: Governance (26 issues), Provider behavior (19 issues) and Contract (13 issues). This stresses the challenges customers face in terms of directing and managing the transaction, the potential hazardous relationship with a third party and the central role of the outsourcing contract as the fundamental instrument that structures and ultimately arbitrates the transaction. Concerning the stages of the outsourcing process we find a more balanced distribution, although jointly the relational categories gather the largest number of references, indicating that part of the negative outcomes may be traced to relational issues.
A complementary analysis of the customer-side dangers is to sort the issues by stage of the IS outsourcing process. Based on the risk elements found in literature, this reveals a dominance of governance focus issues during the decision, relationship building, and relationship management stages; a conjunction of capability, governance, and provider behavior issues during the provider selection stage; the relevance of provider capability during relationship structuring; and the impact of provider behavior issues, closely followed by contract and governance related issues on the outcomes of an IS outsourcing process for the customer.
Table 3: Customer-side Dangers
The fifty five factors that have resulted from the interpretation of the reviewed literature on IS outsourcing risks are presented in Table 4. This is the construct category where the issues have distributed more evenly over the six outsourcing process stages. Two factors—experience and expertise with IS outsourcing—are present throughout the lifecycle of outsourcing, with customer’s expertise being the most cited factor. The majority of the factors (30) have locus on the customer, followed by 20 factors related to the transaction and five factors being attributes of the provider. Concerning the issues with customer locus, the two major focus categories are Governance (14 factors), comprising a set of issues that shapes the perspective customers hold on outsourcing, followed by Capability (11 factors), as measures of the customer’s skills and competences on IS outsourcing.
To a certain extent, this list of factors provides a means for a customer to evaluate its current stand with respect to the fulfillment of the conditions for enabling a successful IS outsourcing transaction. Indeed, by self-diagnosing itself in the majority of the factors, and by judging provider related characteristics and outsourcing transaction features, the customer may get a better understanding of the present weaknesses and be in a better position to decide if meets the conditions to go ahead with the outsourcing or if is able to improve certain attributes in order to compensate some imbalance both in terms of know-how or power in relation to the provider.
Table 4: Customer-side Factors

The analysis of the collected works resulted in the consolidation of 127 mitigation actions which are listed in Table 5. This is the construct with the largest pool of instances, although no single issue clearly stands out over the rest. Yet, the analysis by focus shows a strong incidence of the mitigation actions in governance related practices (Transaction Control and Project Management), followed by the Relationship and Capability categories. As it might be expected, the stage Outcomes does not contain any issue, highlighting the reasoning that mitigation actions must be timely implemented.
A note of caution regarding this list is that some of the actions advanced in literature are actually goals, instead of specific means that may diminish the severity of negative outcomes. This implies that some items classified as risk mitigation actions would benefit from a concretization, by indicating specific actions that might contribute to the achievement of the formulated goal. Indeed, for some of these items, it might be possible to interpret them as inverse negative outcomes.
Table 5. Customer-side Mitigation Actions
4.2 Provider Side View
The analysis of the collected literature clearly showed an imbalance between the works that identify IS outsourcing risk elements related to the customers and those related to providers. Indeed, of the 34 papers analyzed, only four list risks from the perspective of the provider, and of those, only two are totally dedicated to the risks of IS outsourcing from the standpoint of providers. Actually, of the 727 risk elements that we found in the literature, 693 consist of issues related to the customer, and only 34 regard the provider side (a proportion of 19:1). Consequently, the richness and diversity of the catalog from the provider side is much lower when compared to the customer side. Although this might be understandable, given the greater number of potential customers in the market in comparison to the number of providers, we argue for the need to perform further research on IS outsourcing risks from the provider’s standpoint.
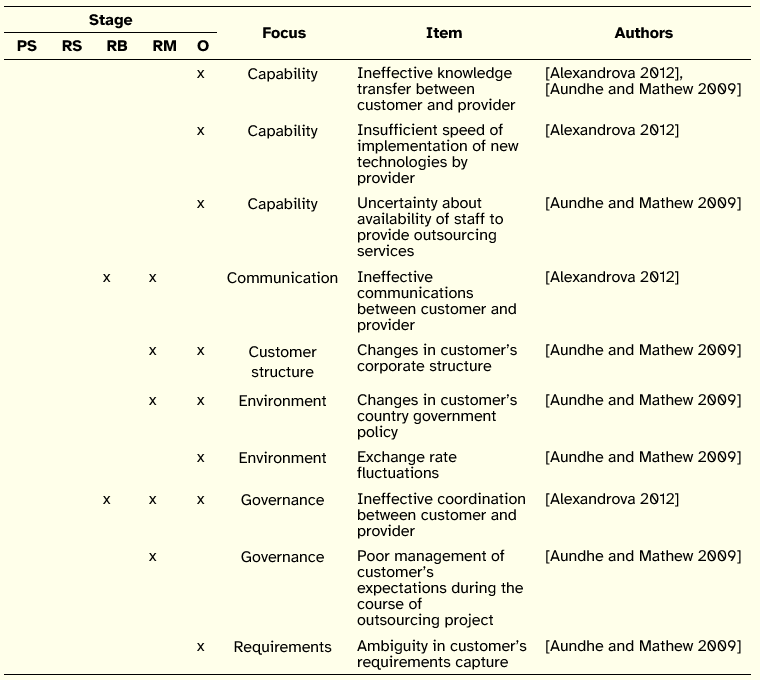
In what concerns dangers, the analysis resulted in 10 issues, listed on Table 6. Three of those issues have a focus on Capability, two on the Environment, and two on Governance. With the exception of two issues, the other dangers have an impact on the outcomes stage. None of the dangers were placed on the Provider Selection or Relationship Structuring stages. The set of dangers are based on the works [Aundhe and Matthew 2009] and [Alexandrova 2012], the two studies that contemplated the IS outsourcing risk topic from the perspective of the provider.
Table 6: Provider-side Dangers
The provider-side factors are in number of 13 and show a more balanced distribution between the five stages of the IS outsourcing process from the perspective of the provider, as can be observed in Table 7. Their locus is also well distributed between Customer, Provider and Transaction. In terms of focus we found Capability has the most represented class.
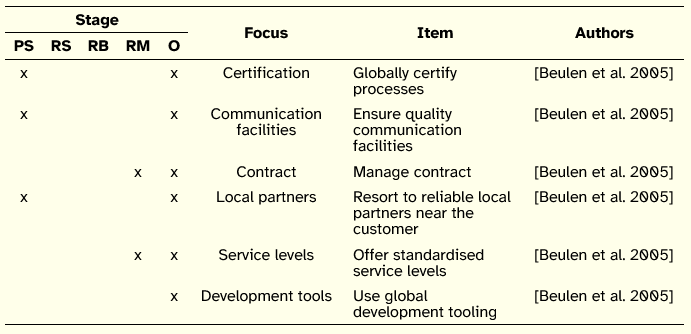
Finally, regarding mitigation actions, we found just one work that explicitly advanced mechanisms for providers to reduce the impact of IS outsourcing risks. The six issues, listed in Table 8, have all different focus, and none has an impact on the stages of Relationship Structuring and Relationship Building. Although some of the risk mitigation actions may have an impact on more than one stage, all of them were classified as enabling the reduction of risk on the Outcomes stage of IS outsourcing.
Table 7: Provider-side Factors
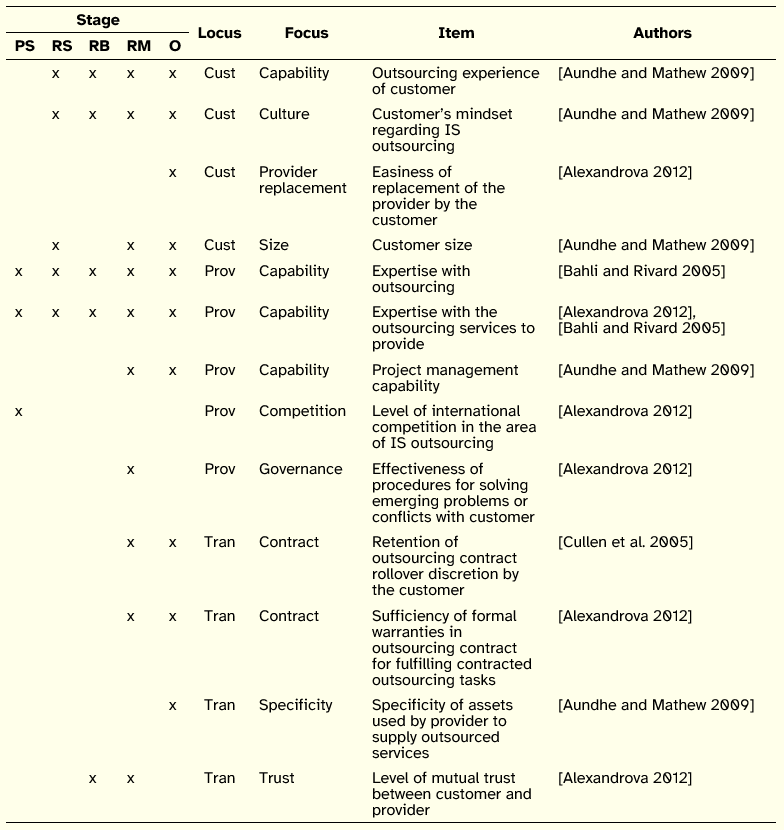
Table 8: Provider-side Mitigation Actions
5. Conclusion
The search for a theory of IS outsourcing risk is a long and difficult endeavor. In this paper we attempted to begin attacking that challenge by proposing a conceptual framework comprising the main constructs of the theory and by elaborating a catalog of IS outsourcing risks based on literature. This catalog is structured in two parts—the customerside view and the provider-side view, which in turn are composed by five sets of classified risk elements, namely dangers, negative outcomes, factors, mitigation actions, and undesirable consequences.
For practitioners this catalog offers a systematic review and classification of the IS outsourcing risks found on the literature. This artifact may prove useful for those considering outsourcing the management or operation of theirs IT assets or activities, those seeking to market their outsourcing services, and those that already embarked in such a transaction. By foreseeing important elements influencing the success of an outsourcing process, the artifact may assist practitioners performing the corresponding IS outsourcing risk analysis, self-diagnosing weaknesses, drawing attention to possible future troubles, and helping to understand how certain outcomes materialized.
For researchers, we think that the catalog can form a basis on which to build research efforts that may finally lead to the synthesis of an IS outsourcing risk theory. The catalog was developed according to a conceptual framework that we believe capture the main distinctions of the risk concept. Moreover, the catalog holds on an extensive review of the existing literature that explicitly addressed IS outsourcing risks, not only listing, but also condensing and categorizing each of the risk elements present in the literature reviewed.
Nevertheless, this work has several limitations. One cannot consider the catalog as exhaustive or complete. Probably, it will never be a complete artifact—it is possible that new risks emerge, new factors have to come into play, and new mitigation actions have to be devised. Additionally, different types of IS outsourcing may have associated specific subsets of risks, a situation that the presented catalog does not address, since it treats indistinctly outsourcing varietals. A third limitation is the subjective interpretation underlying the condensing and categorization of each of the risk elements found on the literature. Although we tried to minimize this limitation by splitting the analysis of risk elements among the authors and by allocating blocks of risk elements to more than one of the authors in order to evaluate and improve the reliability of the analysis, there may still be room for discordant interpretations.
The move towards the generation of an IS outsourcing theory admits (and requests) many future works. At the conclusion of this study we advance six avenues for research. One is to complement the part of the catalog related to the provider’s viewpoint. In possession of a more rich categorization of the IS outsourcing risks from the perspective of the providers, we would be able to relate the risk perspectives of the two stakeholders in an IS outsourcing transaction. A second suggestion is to complement the constructs danger and negative outcome with a risk profile. Recognizing the operational difficulty of adopting an approach that could take into account the contingencies of a specific customer or provider, an alternative way to assist in risk profiling might be to assess the possibility of dangers and negative outcomes by indexing it to the factors. A third proposal for future research is to conduct a field study in order to assess the comprehensiveness of the catalog. This could consist of a retrospective study of a series of IS outsourcing cases in the risk sphere. The fourth proposition involves equalizing the granularity o f the issues that instantiate each of the constructs that make up the catalog. An additional idea for future work derives from the complementary view of risk as opportunity that can produce gains. Adopting this view, where IS outsourcing benefits are conceived as (eventually positive) risks, one could extend the theory to encompass the interplay between IS outsourcing dangers and opportunities. The final suggestion is to pursue in full extent the structure of the conceptual framework. Besides proposing the fundamental constructs of interest in the realm of IS outsourcing risks, the conceptual framework establishes a relationship between the constructs. The test and exploration of the relationships between the items composing the catalog, namely between issues pertaining to the construct factor and to the construct danger, danger and negative outcome, mitigation action and negative outcome, and negative outcome and undesirable consequence, would effectively constitute a network of connections between the items, and substantiate a theory of IS outsourcing risk.
References
Abdullah, L. M. and J. M. Verner (2012). Analysis and application of an outsourcing risk framework. Journal of Systems and Software 85(8), 1930–1952.
Ackermann, T., A. Miede, P. Buxmann and R. Steinmetz (2001). Taxonomy of Technological IT Outsourcing Risks: Support for Risk Identification and Quantification. Proceedings of the Nineteenth European Conference on Information Systems. Paper 240.
Alexandrova, M. (2012). IT Outsourcing Risks: Empirical Evidence from Bulgarian Service Providers. Proceedings of the Virtual International Conference on Advanced Research in Scientific Fields—ARSA 2012, 29–33.
Apte, U. M., M. G. Sobol, S. Hanaoka, T. Shimada, T. Saarinen, T. Salmeal and P. J. Vepsalainen (1997). IS outsourcing practices in the USA, Japan and Finland: a comparative study. Journal of Information Technology 12(4), 289–304.
Aron, R., E. K. Clemons and S. Reddi (2005). Just Right Outsourcing: Understanding and Managing Risk. Journal of Management Information Systems 22(2), 37–55.
Aubert, B. A., M. Patry and S. Rivard (1998). Assessing the risk of IT outsourcing. CIRANO—Centre interuniversitaire de recherché en analyse des organisations. Available: ttps://depot.erudit.org/bitstream/000399dd/1/98s-16.pdf
Aundhe, M. D. and S. K. Mathew (2009). Risks in offshore IT outsourcing: A service provider perspective. European Management Journal 27(6), 418–428.
Bahli, B. and S. Rivard (2003). The information technology outsourcing risk: a transaction cost and agency theory-based perspective. Journal of Information Technology 18(3), 211–221.
Bahli, B. and S. Rivard (2005). Validating measures of information technology outsourcing risk factors. Omega 33(2), 175–187.
Beulen, E., P. van Fenema and W. Currie (2005). From Application Outsourcing to Infrastructure Management: Extending the Offshore Outsourcing Service Portfolio. European Management Journal 23(2), 133–144.
Chou, D. C. and A. Y. Chou (2009). Information systems outsourcing life cycle and risks analysis. Computer Standards & Interfaces 31(5), 1036–1043.
Cullen, S., P. B. Seddon and L. P. Willcocks (2005). IT outsourcing configuration: Research into defining and designing outsourcing arrangements. Journal of Strategic Information Systems 14(4), 357–387.
Currie, W. L. (1998). Using multiple suppliers to mitigate the risk of IT outsourcing at ICI and Wessex Water. Journal of Information Technology 13(3), 169–180.
Dhar, S. and B. Balakrishnan (2006). Risks, Benefits, and Challenges in Global IT Outsourcing: Perpectives and Practices. Journal of Global Information Management 14(3), 39–69.
Dibbern, J., T. Goles, R. Hirschheim and B. Jayatilaka (2004). Information Systems Outsourcing: A Survey and Analysis of the Literature. The DATA BASE for Advances in Information Systems 35(4), 6–102.
Doty, D. H. and W. H. Glick (1994). Typologies as a Unique Form of Theory Building: Towards Improved Understanding and Modeling. Academy of Management Review 19(2), 230–251.
Earl, M. J. (1996). The Risks of Outsourcing IT. Sloan Management Review 37(3), 26–32.
Fan, Z. P., W. L. Suo and B. Feng (2012). Identifying risk factors of IT outsourcing using interdependent information: An extended DEMATEL method. Expert Systems with Applications 39(3), 3832–3840.
Gandhi, S. J., A. Gorod and B. Sauser (2012). Prioritization of outsourcing risks from a systemic perspective. Strategic Outsourcing: An International Journal 5(1), 39–71.
Gartner (2013). Press Release—Gartner Says Worldwide IT Outsourcing Market to Reach $288 Billion in 2013. Gartner, Inc. July 17.
Gartner (2014). Forecast Analysis: IT Outsourcing, Worldwide, 1Q14 Update. Gartner, Inc. April 14.
Gonzalez, R., J. Gasco and J. Llopis (2005). Information systems outsourcing risks: a study of large firms. Industrial Management & Data Systems 105(1), 45–62.
Gonzalez, R., J. Gasco and J. Llopis (2009). Information systems outsourcing reasons and risks: an empirical study. International Journal of Human and Social Sciences 4(3), 181–192.
Gregor, S. (2006). The Nature of Theory in Information Systems. MIS Quarterly 30(3), 611–642.
ISO (2009). ISO 31000—Risk management—Principles and guidelines. International Organization for Standardization.
Iacovou, C. L. and R. Nakatsu (2008). A Risk Profile of Offshore-Outsourced Development Projects. Communications of the ACM 51(6), 89–94.
Jurison, J. (1995). The role of risk and return in information technology outsourcing decisions. Journal of Information Technology 10(4), 239–247.
Kerlinger, F. R. (1986). Foundations of Behavioral Research, third edition. Orlando, USA: Harcourt Brace Jovanovich College Publishers.
Kern, T. and L. P. Willcocks (2001). The Relationship Advantage: Information Technologies, Sourcing, and Management. Oxford, UK: Oxford University Press.
Kern, T., L. P. Willcocks and M. C. Lacity (2002). Application Service Provision: Risk Assessment and Mitigation. MIS Quarterly Executive 1(2), 113–126.
Khidzir, N. Z., A. Mohamed and N. H. Arshad (2013). ICT Outsourcing Information Security Risk Factors: An Exploratory Analysis of Threat Risks Factor for Critical Project Characteristics. Journal of Industrial and Intelligent Information 1(4), 218–222.
Knight, F. H. (1921). Risk, Uncertainty, and Profit. Boston, USA: Houghton Mifflin Company.
Lacity, M. C. and R. Hirschheim (1993). The Information Systems Outsourcing Bandwagon. Sloan Management Review 35(1), 73–86.
Lacity, M. C., S. A. Khan and L. P. Willcocks (2009). A review of the IT outsourcing literature: Insights for practice. Journal of Strategic Information Systems 18(3), 130–146.
McIvor, R. (2008). What is the right outsourcing strategy for your process? European Management Journal 26(1), 24–34.
Renn, O. (1992). Concepts of Risk: A Classification, In Krimsky, S. and S. Golding (Eds), Social Theories of Risk. Westport, USA: Praeger, 53–79.
Sabherwal, R. (1999). The role of trust in outsourced IS development projects. Communications of the ACM 42(2), 80–86.
Sakthivel, S. (2007). Managing Risk in Offshore Systems Development. Communications of the ACM 50(4), 69–75.
Slovic, P. (1999). Comment: Are trivial risks the greatest risks of all? Journal of Risk Research 2(4), 281–288.
Tafti, M. H. A. (2005). Risks factors associated with offshore IT outsourcing. Industrial Management & Data Systems 105(5), 549–560.
Varajão, J., C. Pereira, L. Amaral and S. Castro (2011). Outsourcing de serviços de sistemas de informação na banca em Portugal. Computerworld.
Varajão, J., R. Gonçalves, L. Barroso and L. Amaral (2006). Outsourcing de serviços de sistemas de informação. Revista Dirigir—Separata, 93.
Vassiliadis, B., A. Stefani, J. Tsaknakis and A. Tsakalidis (2006). From application service provision to service-oriented computing: a study of the IT outsourcing evolution. Telematics and Informatics 23(4), 271–293.
Whitten, D. and R. L. Wakefield (2006). Measuring Switching Costs in IT Outsourcing Services. Journal of Strategic Information Systems 15(3), 219–248.
Willcocks, L. P. and M. C. Lacity (1999). IT outsourcing in insurance services: risk, creative contracting and business advantage. Information Systems Journal 9(3), 163–180.
Willcocks, L. P., M. C. Lacity and T. Kern (1999). Risk mitigation in IT outsourcing strategy revisited: longitudinal case research at LISA. Journal of Strategic Information Systems 8(3), 285–314.