Original source publication: Soares, D. and F. de Sá-Soares (2014). Information Systems Security Management Key Issues in Local Government. Proceedings of the International Conference on Electronic Government 2014—ICEGOV 2014. Guimarães (Portugal).
The final publication is available here.
Information Systems Security Management Key Issues in Local Government
Universidade do Minho—Centro ALGORITMI, Departamento de Sistemas de Informação, Guimarães, Portugal
Abstract
Information systems security plays a central role in the provision of services by Public Administration agencies. To foster a trust climate in the development of e-government, it is important to know the main concerns when managing initiatives to protect information assets. The aim of this research in progress is to identify and prioritize the key issues that Local Government chief information officers face, or believe they will face in the near future, in the domain of information systems security management.
Keywords: Key Issues; Information Systems Security Management; Local Government Information Systems Security
1. Introduction
One of the challenges facing public administration agencies concerns the need to adequately manage their information assets. This is particularly critical with regard to safeguarding the privacy and data of citizens, ensuring the availability of such data and their integrity and accuracy [Palanisamy and Mukerji 2014]. Indeed, much of the information collected, stored and made available by agencies, whether referring to their employees or to people and organizations to which they provide services, has a personal and private nature. Hence, it is essential that there are security controls which protect information systems (IS) from a myriad of threats, such as unauthorized access or modification, disclosure, destruction and repudiation [Kraaijenbrink 2002]. This call for action is increasingly pressing: from 2007 to 2012 data breaches in UK local government have risen by 1,609% [CFS 2012] and from 2009 to 2013 the number of reported security incidents by USA federal agencies more than doubled, reaching more than 60,000 incidents in 2013, of which almost 25,000 involved personal identifiable information [GAO 2014].
The issues related to information systems security (ISS) are recurrently presented as a major barrier or critical factor to the development of e-government [Eyob 2004; Venkatesh et al. 2012]. The perception that citizens may have regarding the lack of adequate security levels in the electronic processes used within Public Administration agencies and between citizens and those agencies, can generate levels of mistrust that ultimately compromise the use of public electronic services. The establishment of a climate of trust can be achieved by using a set of security mechanisms, ranging from risk analysis and formulation of security policies to the implementation of security procedures and security technologies such as passwords, firewalls, intrusion detection systems, and encryption [ISO/IEC 2013].
The importance of ISS and the difficulty of its management become even more significant in the case where the provision of integrated services to citizens is based on the interoperability between different IS, especially when its implementation requires information transfer and sharing among various agencies [Evangelidis et al. 2002; Kraaijenbrink 2002].
The challenging complexity and variety of public agencies, their intensive use of information and information technology (IT), and their need to effectively protect information assets, motivated us to study the activity of ISS management in the realm of Public Administration, focusing our attention on Local Government, given its proximity to citizens. Thus, the aim of this study is to identify and prioritize the key issues that Local Government chief information officers (CIOs) face, or believe they will face in 5 to 10 years, in the domain of ISS management.
This paper is organized as follows. After this introduction, we explain the study design, giving special attention to the planning of the research. Then, we present the findings that resulted from the first moment of data collection in the field. We conclude with a preview of the subsequent steps of this research in progress.
2. Study Design
The identification of the main aspects concerning the management of IS and IT from the perspective of practitioners is a topic that has attracted the attention of various researchers. As illustrative of this observation, the USA based Society for Information Management (SIM) commissioned fifteen surveys between 1980 and 2013 with the aim of uncovering the key issues that its members were facing when managing IS/IT (cf. [Ball and Harris 1982] and [Kappelman et al. 2013] as two exemplifying studies in that series of works). Over that period of time, the interest in identifying key issues expanded to other countries and diversified into other areas of research.
In 2013, Polónia and de Sá-Soares [2013] published a study where the key issues that ISS managers face, or believe they will face, in the near future were identified and prioritized. To the best of our knowledge, this was the first key issues study that targeted the ISS management activity, with those authors suggesting as future work the promotion of similar studies by restricting respondents to specific industries or sectors. This current work embraces that challenge selecting as targets Local Government chief information officers.
Since our research goal was to replicate that study for Local Government, and with the intention to undertake a comparative analysis between its results and this work, we built on that research, adopting its main tenets, namely from a methodologically point of view. Therefore, we adopted the Delphi method and resorted to the Q-sort technique.
The Delphi method consists of a series of questionnaires (called Delphi rounds) directed to a group of experts (the Delphi panel) in a given phenomenon. After the initial round, the promoters of the Delphi provide experts with a summary of the aggregate opinion of the panel and ask them to re-examine their answers to the previous round taking into account that aggregate opinion. Then, a new round of the Delphi study takes place. This procedure may be further repeated. The goal of the application of the Delphi method is to reach a consensus among the participant experts. However, if a consensus if not achieved, then the Delphi results may still prove useful, since they may uncover divergent points of view among respondents, providing a basis for further inquiry into the phenomenon under scrutiny.
Considering that our aim was not only to identify the ISS management key issues in the view of Local Government CIOs, but also to rank those issues by order of importance, we also coupled the Delphi method with the Q-sort technique. Consisting of a systematic way of rank-ordering objects, the Q-sort technique creates the conditions for an evaluator to rank a set of objects (in this case issues related to ISS management in Local Government) as a whole, avoiding the consideration of individual objects without taking into account the remaining objects, as it is usually the case when classifying objects via Likert scales.
The planning of the Delphi study involved decisions regarding the constitution of the panel, the design of the rounds, the communication with the experts and the definition of stop criteria.
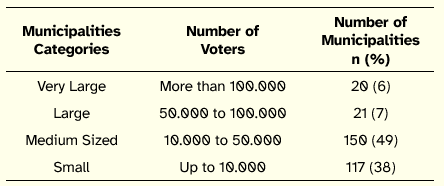
In this study the potential constituents of the Delphi panel were Local Government CIOs. For the sake of feasibility and validity of findings in terms of cultural and regional similarity, we decided to instantiate the panel to the Portuguese Local Government. At the present, Portugal has 308 Municipalities, which form the Local Government level of Portuguese Public Administration, distributed by size of electorate as illustrated in Table 1. We sent an email message to the 308 Municipalities presenting the study, describing its aims and inviting them to participate in it.
Regarding the design of the Delphi rounds we had several options. The first decision concerned the use of a predefined list of issues to present the panel for classification or the option for a blank list, where respondents would be asked to provide six to ten concerns regarding ISS management. To reduce the cognitive effort of participants, and given that we were replicating study [Polónia and de Sá-Soares 2013], we chose to present respondents a predefined list of issues. We used as preliminary version of this list the final list of key issues resulting from study [Polónia and de Sá-Soares 2013], which was composed of 26 aspects concerning ISS management and corresponding brief descriptions. We reviewed the formulation of those issues and descriptions, adapting their phrasing to the context of Local Government, e.g., replacing references to customers by citizens, top management by Town Council Executive, and organization by Town Hall. The items composing this list were presented to participants randomly ordered in the initial round of the Delphi. To prevent the possibility of this list still conveying a vision biased to general business, we decided to keep the first round open. This means that respondents, after classifying in terms of importance the 26 items composing the initial list of issues, were given the opportunity to add issues that they thought were missing from that list and that they considered relevant in the realm of their context and experience in managing ISS. A third decision was to not remove the less important issues after each round, unless the number of new issues suggested by the panel in the first round would make this option prohibitive in terms of effort. In order to expedite the collection of the data required by each Delphi round, and to enforce the rules of the Q-sort technique, we used a Web application to administer the Delphi surveys.
The protocol used to communicate with participants was also defined. An email message would be sent to each participant in the beginning of each round. This message would recall the purpose of the study and inform on the period for answering the survey, the Web link and the credentials required to participate in the round, an assurance for confidentiality and anonymity, the email and phone contacts of the research team, and for the rounds after the first one, a synthesis of the consensus achieved in the previous round. Two email reminders would be sent to those participants that had not answered the survey.
3. Preliminary Results
In this section we present preliminary findings of this work, namely the results derived from the first round of the Delphi study.
From the 308 invited Municipalities to participate in this study, in the first round we got answers from 69 CIOs, corresponding to a response rate of 22%. In terms of size of Municipality by electorate, the 69 participants are distributed as shown in Figure 1. This configuration of respondents is in line with the distribution presented in Table 1, enabling the results to reflect more accurately the total pool of experts.
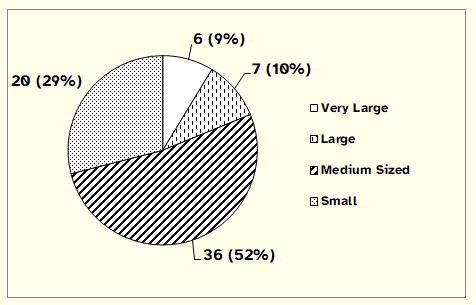
Figure 1: Distribution of Respondents by Size of Electorate
At the end of the first round the panel ranked the 26 issues as presented in Table 2. This aggregate view of the importance of the issues forming the initial list of ISS management concerns has associated a Kendall’s W of 0.134 (p < 0.001). Although the interpretation of W is not a straightforward task, we will follow Schmidt [1997] suggestion and consider that value represents weak agreement among the panel’s members. To a certain extent this was expected, since the initial round consisted of the first contact of the participants with the list of issues and the respondents still did not have available the opinion of the panel as a whole to help fostering a higher level of consensus. We note that for the first round, it makes no sense to determine Kendall’s T.
Besides the 26 items composing the initial list of issues, we observe in Table 2 the appearance of two new issues. These issues were advanced by two participants, who also provided a brief explanation for their suggestions, a situation made possible since the first round was open to the inclusion of new items. One of these two new issues is related to the updating of the ISS plan and the other to the existence of an organizational role or unit in the Town Hall responsible for managing the IS protection efforts. There is no rank associated to each of these issues since the panel has not yet had the opportunity to classify them.
Table 2: Results after First Round of Delphi
† Issues suggested by participants
na (not applicable)

At this intermediate stage of the research process any analysis and discussion of the findings, although possible, should be always considered as tentative and subject to eventual disconfirmation by subsequent data collection and analysis phases. With this limitation in mind, a first approach to the analysis of the ranked list of issues is to divide them into four groups, according to the distance each issue is placed from the first issue ranked by using the corresponding average. Hence, the first group of most important issues includes items ranked 1 to 4 (up to 1.5x average of first ranked issue), the second group of important issues are the items ranked 5 to 10 (up to 2.0x average of first ranked issue), the third group of medium importance issues the items ranked 11 to 21 (up to 2.5x average of first ranked issue) and the group containing the least important issues including items 22 to 26 (up to 3.0x average of first ranked issue). Taking into account the rank of each issue and the associated average of the Q-sort classification allows a more detailed understanding of the positioning of each issue.
Considering the group containing the most important issues, we observe that respondents placed near the top of the list two issues concerning two basic requirements of ISS–availability (issue 1) and confidentiality (issue 4), accompanied by the capability to detect ISS anomalies (issue 3) and, as the second most important issue, the ability to control the use of electronic devices that can manipulate sensitive information of the Town Hall, suggesting a high concern with the challenge of maintaining a security perimeter in the context of an ever growing IT mobile world.
Another approach to the analysis of the ranked list is to compare it with the final ranking obtained in [Polónia and de Sá-Soares 2013]. To facilitate this comparison, we included that ranking in Table 2 (cf. column 4). The first regularity observed is that the same issue ranked first, emphasizing the importance given to the ability to recover IS and information both for firms and Town Halls alike. In the first four ranked issues we find other similarities between the studies (although not as striking as for issue 1), but also a substantial difference regarding issue 2 in this study, which ranked 17th in [Polónia and de Sá-Soares 2013]. The second most relevant distinction between the two studies is the issue placed seventh (25th in [Polónia and de Sá-Soares 2013]), regarding banning access to Internet content with potential risk of causing ISS breaches. Four additional differences are noteworthy between the studies: making contract vendors and service providers responsible in case of ISS breaches (10th in this study against 26th in [Polónia and de Sá-Soares 2013]), getting the commitment of top executives to the ISS effort (14th against 3rd in [Polónia and de Sá-Soares 2013]), validating the effectiveness of the implemented ISS measures (16th against 4th in [Polónia and de Sá-Soares 2013]) and aligning ISS policies with the strategy of the organization (19th against 5th in [Polónia and de Sá-Soares 2013]). If these findings are maintained along the study, this may suggest significant differences in terms of context and set of challenges confronting Local Government CIOs, requiring in-depth inquiry to identify the underlying reasons.
4. Next Steps
According to research plan, we launched the second round of the Delphi study. The panel ranking of issues obtained at the end of the first round was made available to respondents with the aim of converging to a higher level of consensus. The two new issues are also part of the updated list of issues, now closed and totalizing 28 ISS management concerns.
Eventually, the final ranking of issues may suggest post-Delphi research efforts, such as interviews or focus groups, aimed to get a better understanding of the position of certain ISS management concerns in the context of Local Government. These efforts may provide a more substantive interpretation of the final results, helping to clarify the role of factors such as security governance, overall e-government architecture, interoperability frameworks, centralization of e-government services, transparency pressures, and open government data initiatives, to name a few.
Ackowledgments
This work has been supported by FCT—Fundação para a Ciência e Tecnologia within the Project Scope: PEst-OE/EEI/UI0319/2014.
References
Ball, L. and R. Harris (1982). SMIS Members: A Membership Analysis. MIS Quarterly 6(1), 19–38.
CFS (2012). UK data leaks rise 1,000% in five years. Comput Fraud Security 9, 20.
Evangelidis, A., J. Akomode, A. Taleb-Bendiab and M. Taylor (2002). Risk Assessment & Success Factors for e-Government in a UK Establishment. Proceedings of the 1st International Conference on Electronic Government, 395–402. Aix-en-Provence (France).
Eyob, E. (2004_. E-government: breaking the frontiers of inefficiencies in the public sector. Electronic Government an International Journal 1(1), 107–114.
GAO (2014). Information Security: Federal Agencies Need to Enhance Responses to Data Breaches. GAO-14-487T. http://www.gao.gov/assets/670/662227.pdf
ISO/IEC (2013). ISO/IEC 27002:2013—Information technology—Security techniques—Code of practice for information security controls. ISO.
Kappelman, L., E. McLean, J. Luftman and V. Johnson (2013). Key Issues of IT Organizations and Their Leadership: The 2013 SIM IT Trends Study. MIS Quarterly Executive 12(4), 227–240.
Kraaijenbrink, J. (2002). Centralization Revisited? Problems on Implementing Integrated Service Delivery in The Netherlands. Proceedings of the 1st International Conference on Electronic Government, 10-17. Aix-en-Provence (France).
Palanisamy, R. and B. Mukerji (2014). Security and Privacy Issues in E-Government. Cyber Behavior: Concepts, Methodologies, Tools, and Applications, 880–892. Hershey: IGI Global.
Polónia, F. and F. de Sá-Soares (2013). Key Issues in Information Systems Security Management. Proceedings of the 34th International Conference on Information Systems. Milan (Italy).
Schmidt, R.C. (1997). Managing Delphi surveys using nonparametric statistical techniques. Decision Sciences 28(3), 763–774.
Venkatesh, V., F. K. Y. Chan and J. Y. L. Thong (2012). Designing e-government services: Key service attributes and citizens’ preference structures. Journal of Operations Management 30(1-2), 116–133.