Original source publication: Pereira, L., F. de Sá-Soares and M. Caldeira (2012). Information Systems Security Outsourcing Key Issues: A Service Providers’ Perspective. Proceedings of the European Conference on Information Systems 2012, Paper 121. Barcelona (Spain).
The final publication is available here.
Information Systems Security Outsourcing Key Issues: A Service Providers’ Perspective
a ISEG—Technical University of Lisbon, Lisbon, Portugal
b University of Minho, Guimarães, Portugal
Abstract
There is a perception that information systems security outsourcing, in spite entailing a relationship between a client and one or more providers, tends to be studied and analysed from the perspective of the client. A gap is then believed to exist in the study of the information systems security outsourcing relationship from the point of view of the service provider. This research aims to identify the key issues of such a relationship from the perspective of the service provider and rank them according to their importance. The Delphi method was used to support the communication with the group of experts contributing to this research as well as to boost consensus within the group. Final interviews with participants were also conducted with the aim of reaching deeper into their opinions and to shed a brighter light over the results of the Delphi. A ranked list of the 13 most important key issues found is presented and discussed and propositions for further work are put forward in the wake of the study.
Keywords: Information Systems Security Outsourcing; Information Systems Security; Key Issues Study; Delphi Method
1. Introduction
The information systems security (ISS) outsourcing relationship, as any relationship, presupposes the existence of two or more parties. This type of relationship is formally instantiated in the form of contracts between the party that resorts to outsourcing (the client) and the ones performing the activities outsourced (the service providers).
If the benefits of outsourcing are to be attained, the success of such relationships is paramount. That is why this study aims at unveiling which are the key issues in creating and maintaining a successful ISS relationship between client and service provider. Former studies usually take on the client’s point of view, but, although that is an important point of view, the service providers’ point of view seems to be lacking the insight which this study intends to fulfil.
The study aims to find key issues towards a successful ISS outsourcing relationship from the perspective of the service providers and rank those issues according to their importance.
It is believed that this research is of particular importance due to the delicate nature of its subject (outsourcing of ISS activities by organizations) but also in deepening the understanding of the ISS outsourcing relationship in order for organizations to steer their path in the right direction.
The paper is structured as follows. After this introduction, we review the literature on information systems (IS) outsourcing and on ISS outsourcing. Then, the research design is depicted, which is followed by a description of the study. Finally, we present the main results of the study and discuss them. The paper ends by drawing conclusions and suggesting future work.
2. Literature Review
2.1 Information Systems Outsourcing
The cumulative knowledge on IS outsourcing is significant. In a review of IS outsourcing research, published between 1990 and 2008, Lacity et al. [2009] classified 191 papers into six topics: determinants of IS outsourcing, IS outsourcing strategy, IS outsourcing risks, determinants of IS outsourcing success, client and supplier capabilities, and sourcing varietals.
The most researched topic has been the determinants of IS outsourcing success. The work on this topic can be classified into three categories: the IS outsourcing decision making, contractual governance, and relational governance. Research on IS outsourcing decision making has focused on the degree of outsourcing, top management commitment/support, and the evaluation process for selecting providers. Research on contractual governance has considered four determinants of success related to the outsourcing contract: its detail, type, duration, and size. The studies on relational governance cover soft issues in the client-provider relationship management, including trust, norms, communication, sharing of information, mutual dependency, and cooperation.
Closely linked to these determinants are the client and provider capabilities. These include overall capabilities such as IS technical/methodological capability, IS human resource management capability, provider management capability, contract management capability, domain capability, IS change management capability, transition management capability, and client management capability.
2.2 Information Systems Security Outsourcing
IS security outsourcing may be understood as the transfer of an existing in-house IS security function to a third-party provider [Fenn et al. 2002], as a whole or partially. The benefits that may be achieved by a client through an ISS outsourcing arrangement include cost savings, access to high expertise, improved service performance, extra capacity to react to security incidents, increased capability to focus on core business competencies, and staffing flexibility [Allen et al. 2003; Endorf 2004; Schneier 2002].
However, the decision for ISS outsourcing is not risk free. Among the disadvantages that an organization may face are breaches of confidentiality, upfront investment [Fenn et al. 2002], stealing of proprietary information, and opportunistic repricing of contract terms after the provider feels locked-in [Rowe 2007]. Beyond these, it may be added the risks of partnership failure, unanticipated hidden costs and impacts, and legal issues [Allen et al. 2003].
As with IS outsourcing, the management of the ISS outsourcing relationship has attracted the interest of researchers. Fenn et al. [2002] argue that outsourcing ISS is only as effective as the relationship between the provider and the client: finding the right provider and agreeing appropriate and workable service levels are of paramount importance.
Recognizing that outsourcing success does not depend only on contractual aspects but also on the relationship established between the parties, Tsohou et al. [2007] identified six factors affecting ISS outsourcing outcome: participation, communication, mutual understanding, information sharing, top management support, and coordination. Although it is possible to draw a parallel between these factors and the determinants of IS outsourcing success, Karyda et al. [2006] argue that ISS outsourcing presents its own features and challenges and it should be examined using a different lens.
Regarding the division of work between the outsourcing parties, Alner [2001] advocates that great attention must be given to determining which parts of the ISS function should be performed by the provider and which should be handled by the client.
To Endorf [2004], successfully managing ISS outsourcing involves following best practices, conducting due diligence, specifying requirements, and defining roles and responsibilities.
In what concerns ISS outsourcing providers’ required features, Endorf [2004] argues that it is generally better to deal with a provider with which a relationship already exists. Power and Forte [2005] focus on assuring the provider has a well trained staff in the functions they would be performing and that it can independently assess the professional qualifications of their security-related personnel. Schneier [2002] advises on avoiding situations of conflict of interest by service providers (e.g., sell and manage security products).
The survey of the literature suggests that ISS outsourcing is a somewhat unexplored area in IS at large. The rare occurrences of papers dealing with this topic tend to assume the client’s perspective leaving the service provider’s perspective as almost uncharted territory.
Since outsourcing implies a relationship, which automatically requires the existence of two or more parties, and since the point of view of the service provider has somewhat been neglected in academic literature, it makes sense to pursue the research goals set for this study.
3. Research Design
Given the goals of the study and the gap in literature on determinants of ISS outsourcing success from the service providers’ perspective, we selected the Delphi method as research strategy.
Usually, a Delphi study consists of a cycle of rounds where a group of experts in a specific domain are inquired individually and anonymously about issues pertaining to their domain of expertise. Linstone and Turoff [1975] characterize the Delphi method as a structured group communication process that is efficient in allowing individuals to deal with a complex problem. To achieve this structured communication, a measure of feedback is given to participants regarding their own answers and regarding the answer of the group (the Delphi panel) as a whole. This form of inquiry gives participants the possibility of correcting or revising their answers.
Since the study required not only the identification of the key issues, but also the ranking of those issues in terms of importance, we combined the Delphi method with Q-sort technique. The use of this technique facilitates the ordering procedure by participants, since they have to consider all the issues as a whole (mitigating the isolated consideration of issues), to divide them into three groups (the most important, the least important, and the neutral ones) and to rank them according to a predetermined quasi-normal distribution.
The Delphi method is essentially qualitative in its approach but resorts to quantitative tools in what comes to determining what are the most and least important issues and to assessing the degree of consensus within the group.
The decision to rely on the Delphi method and the Q-sort technique as research tools capable of allowing the study to reach its goals was taken due to several reasons, namely:
The exploratory nature of the study, where the problem cannot be initially solved by analytical techniques, but can benefit from subjective collective judgments;
The study dwells upon judgments that allow group involvement or a group decision process may boost the outcome of the study and reinforce its findings;
Time and cost do not allow frequent face to face meetings;
The past application of the Delphi method to studies with similar objectives such as the key issues studies by Brancheau and Wetherbe [1987] and Brancheau et al. [1996].
In setting up the Delphi rounds, six tasks were completed before the rounds cycle could effectively start, namely the selection and invitation of experts to form the Delphi panel, definition of the communication process with experts, decision on the type of rounds, administration of the Delphi method with Q-sort technique, decision on the trimming of issues, and definition of stop criteria.
The process of selecting and inviting experts is extremely important because their ideas and opinions will determine the richness and quality of the study. Besides providing the raw matter to the study, it is the controlled interaction between experts that will enable the study to meet its goals. According to Okoli and Pawlowski [2004], a group of 10-18 experts is acceptable to conduct a Delphi study.
The selection process began by listing a group of 20 companies operating in Portugal that provide ISS services. The targets in these companies were managers and senior consultants working in ISS. Several approaches were applied to compose the expert panel, namely using the researchers’ networks of contacts, searching corporate websites, and resorting to Linkedin to browse for people with the characteristics that were pursuit vis-à-vis their background, experience, and current position.
Invitations to participate were sent and we got an agreement of participation from 14 professionals representing 13 companies. The average work experience of these professionals was 14.4 years (min = 8 years, max = 23 years).
During the study, the communication process with participants would observe the following protocol:
An email initiated each round conveying information about the objective of the round; the time period it would be open to answers; the Web link and credentials that would enable the expert to participate; a guarantee of confidentiality and anonymity; a highlight of the importance of their contribution to the outcome of the study; disclosure of the researchers’ contacts for any unforeseen circumstance; and in rounds after the second one, a brief description of the consensus obtained in the previous round;
To those participants that had not yet responded, a reminder would be sent by email two days before the answering period ended and on the day the answering period ended;
One extension to the answering period would be allowed, never exceeding one week; and
In case of contacts made by participants a timely answer by the research team was mandatory.
In what concerns the type of rounds, we decided to perform a blank sheet first round. The first round of the Delphi process would be used to collect from participants their opinions on what are the key issues surrounding a successful ISS outsourcing relationship. This was seen necessary since no relevant issues were identified in the literature specifically for the case of ISS outsourcing and focusing on the point of view of the service provider. It was also decided to conduct open rounds (in which participants can add new issues they think are relevant) after the blank sheet first round until a round comes in which no issues are added.
A Web tool was used to administer the questionnaires to participants. The use of this tool would give experts flexibility and convenience of answering, speeding up the turnaround time between questionnaires and helping participants abide the rules of the Delphi with Q-sort. It also served as a repository of answers from which data could be retrieved to be analysed by researchers.
A decision was also taken to trim the issues that were considered less important in case the study should extend beyond the second round. This decision was made in order to reduce participants’ cognitive effort during ranking rounds, to motivate them to continue answering the questionnaire, and to assist in the promotion of consensus. The number of issues to trim would be determined taking into account the mean and standard deviation of the issue in the panel global ranking, its mode(s), the number of respondents that scored the issue in the first positions, and the existence of outliers.
The interaction between the experts’ opinions may lead to a varying level of consensus. This level can be calculated but there is a need to determine at which level one considers experts to have reached consensus. Prolonging rounds indefinitely would certainly trigger the law of diminishing returns if experts were to be taxed with too many questionnaires. On the other hand, stopping the study too early could hinder its outcome as well, possibly because no valuable results were attained.
For this study, the set of stopping criteria for judging panels’ consensus had three rules:
Kendall’s W of the round should be equal or greater than 0.7 (this rule establishes a threshold for the consensus between participants in a given round);
Spearman’s rho between rounds should be equal or greater than 0.9 (this rule establishes a threshold for the stability of answers between consecutive rounds); and
If the criteria above were not met when the fourth round is reached then the study will stop at the end of the fourth round (this rules establishes a maximum number of rounds to achieve consensus).
If after the four rounds consensus was not reached, the researchers would try to qualitatively elicit the rationale behind each individual ranking by conducting interviews with participants.
4. Description of Study
The study involved the administration of four rounds of questionnaires and a final interview to the participants of the fourth Delphi round.
4.1 Delphi Rounds
Table 1 summarizes the four Delphi rounds. For each round, it is indicated its type, the number of experts that participated (responses), the number of issues involved, and the values for Kendall’s W and Spearman’s rho where applicable. All the 14 experts that agreed to participate in the study were contacted to take part in each of the four rounds.
Table 1: Summary of Delphi Rounds
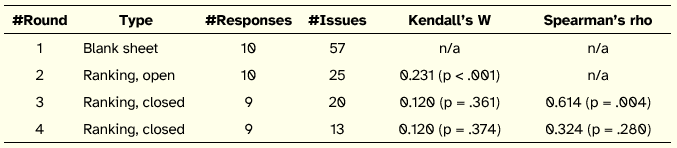
The first round was a blank sheet round, i.e., a round where participants were asked to provide, following the suggestion of Schmidt [1997], at least six issues that, from their point of view, are key to the success of an ISS outsourcing relationship from the service provider’s standpoint. For each issue, participants were also asked to provide a brief description.
The ten experts that contributed to the round suggested 57 issues. These raw issues underwent a process of consolidation by the research team. This process consisted of grouping similar issues beneath an umbrella issue, and formulating a statement to designate the group of issues and a statement to provide a brief description aimed at clarifying the meaning of the overall issue. After a few iterations, this process was considered complete, resulting in a list of 25 consolidated issues.
In the second round participants were asked to rank the list of 25 consolidated issues according to their own point of view. The ranking of issues resorted to the Q-Sort technique which is embedded in the Web tool that mediated the administration of questionnaires. The issues were presented to participants without any meaningful order.
This second round allowed participants to add new issues they thought were missing from the list provided. These new issues would be included in future rounds. None did so which can be an indicator that the consolidation process was good and that the list was considered complete by participants.
The answers to the second round were analysed in relation to their degree of consensus. Kendall’s W was calculated to be 0.231 (p < .001). According to Schmidt [1997], this reveals a weak agreement among experts. Since none of the stopping criteria were met, a third round was promoted.
Before starting the third round two decisions were taken. Since no participant added new issues to the list in the second round, it was decided to no longer allow that possibility to participants and thus the list was considered closed to new issues. The second decision was about reducing the set of issues to be ranked by participants in the third round. The decision was to trim the five issues that were considered less important by the panel in the second round.
The issues were presented to participants in the order of importance given by the panel as a whole in the previous round, from most important to least important.
The outcome of the round was measured in terms of consensus and in terms of convergence between this round and the previous one. Respectively, Kendall’s W was calculated to be 0.120 (p = .361) and Spearman’s rho to be 0.614 (p = .004). This value of Kendall’s W, according to Schmidt [1997], shows a weak agreement among participants and it is in fact worse in terms of consensus than the Kendall’s W calculated in the previous round. Confidence in ranks was quite low. Regarding Spearman’s rho, it shows that although the answer to these two rounds can be correlated positively, a movement occurred between rounds and so it is possible to conclude that the experts’ collective answer did not stay static to a degree that it would be better to stop the study. None of the stopping criteria were met and so a fourth and last round ensued.
Before starting the fourth round a decision had to be taken regarding the reduction of the list of issues to be considered by participants in this round. The first intention was to trim 10 issues off the list. Consensus in the third round was weak and since the fourth was the last round it was considered a good trade-off to reduce the list of issues to 10, boosting the possibilities of consensus by having a shorter list. Deeper analysis of the 10 issues coming last in the third round classification enabled taking a better decision regarding how many issues to trim. Relying only on the relative position of the issues in the ranking to decide on what issues to trim can be misleading because the confidence in ranks is quite low and the active panel was composed of only 10 experts. It was considered relevant to bring to the analysis the mode and how many participants scored that issue in the first 10 positions. This analysis led to the trimming of the last seven issues so the fourth round presented 13 issues to participants ranked according to the importance given to them in the previous round by the panel.
Once again Kendall’s W was calculated together with Spearman’s rho, showing values of 0.120 (p = .374) and 0.324 (p = .280), respectively. Again Kendall’s W showed weak agreement among participants. Confidence in ranks was low. Spearman’s rho showed that the third and fourth rounds can be correlated positively but not to a degree that it could be stated that no change occurred in the experts’ answers. The third of the stopping criteria was met and consequently the questionnaires were halted.
Using descriptive statistics, the fourth round was further analysed with the aim of understanding the dispersion of choice among the various participants. Each issue was analysed considering the best rank position it reached (the minimum), the worst rank position it reached (the maximum), the corresponding range, first quartile, median, third quartile, inter quartile range, and lower and upper limits for outliers. The average inter quartile range was ~5.7 which confirmed the significant dispersion of choice among participants for a set of only 13 issues. The analysis of the lower limits showed that the existence of moderate outliers would be extremely improbable.
4.2 Interviews
After three ranking rounds, consensus among participants was still weak even after reducing the set of issues to rank from 25 to the 13 considered most important by the panel. The analysis had to reach deeper into the motivations and reasons of the participants to answer like they did. We tried to achieve this understanding by interviewing the experts.
Interviews were proposed to the participants of the fourth and last round, and six of them accepted the invitation and had the opportunity to convey their opinions through a telephone interview. The interview script was simple and involved discussing the motivations of the participants to having selected the top three issues they did in the fourth round, prompted by the question Why are they the most important?. Then the panel’s top three issues were conveyed and the possible match or mismatch of opinions was discussed. All experts were interviewed by the first author, who asked experts’ authorization to record the interviews. All the interviewees allowed the recording of the conversation.
In analysing the interviews, the recordings were replayed and every independent aspect mentioned by each interviewee was highlighted. All aspects were then compared and consolidated.
5. Results
The first result of this study is the list of 25 consolidated issues resulting from the first round, presented in Table 2 (issues were classified into five groups that will be discussed in the next section).
Table 2: Consolidated List of Issues

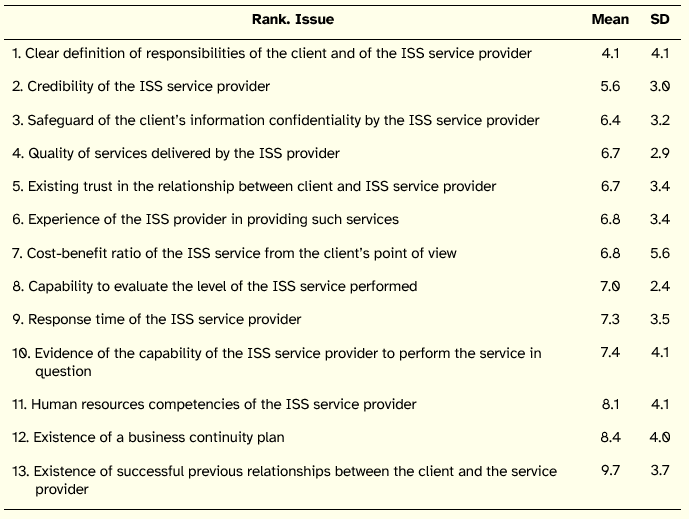
The second result of the study was reached in the end of the fourth round, consisting of the final ranked list of the 13 most important issues from the standpoint of the panel as a whole. Table 3 presents that ranking, along with the mean and standard deviation (SD) for each issue.
Table 3: Final Rank of Issues
The third result of the study derived from the analysis of the interviews. From a general point of view, when addressing their top three issues and the reasons for their choice, participants assumed two perspectives. The more common was seeing the client and the relationship as a future client and a future relationship, which still have to be won. The success factors of the relationship are taken for the issues that enable the selling of the service (cost-benefit ratio, credibility, and experience). This perspective contrasted with the one that focused on the factors that enabled a good ongoing relationship (response time, definition of responsibilities, and the existence of a business continuity plan) and the possibility of assessing the service being provided.
Most participants focused on the price of the service as a key point to win the client and also to maintain the service and the relationship. Issues such as quality of service, experience of the provider, and existence of previous successful relationships take second place behind that factor. The price factor takes precedence when the service being delivered is not differentiated and is seen as a commodity to a large extent. Here the client does not understand the real value of the service and sometimes decision-makers are truly not aware of the value of certain services. For the clients that understand the value of ISS, their demand tends to be based on the quality of the service and not as much on the price.
According to some participants, the motivation for some clients to outsource is the reduction of their costs. This, however, cannot be done successfully if the client does not know itself and does not know its processes. The maturity level of organizations also has to be high enough for them to resort to outsourcing successfully. According to one participant the existence of a business continuity plan is a sign of that maturity.
It was also evident that existed two conflicting views on how ISS outsourcing contracts are celebrated in Portugal. On the one hand, contracts are specific enough to effectively regulate the ISS service and the relationship between client and provider. This point of view tends to see confidentiality, integrity, and availability as premises of the service, enacted in the contract and without room for discussion on their contribution to a successful outsourcing relationship. The opposing view reports contracts as generic, with no specificity regarding ISS and leaves to the provider the responsibility of finding the scope of its service and almost self-regulating. As stated by participants, this may be the evidence of different maturity levels between organizations.
When participants confronted their answers to the fourth round with the group’s answer, almost without exception, they tended to relate their own choices with the ones of the group. In fact, issues are not mutually exclusive and have some overlapping that cannot be excised. For example, trust can be related to credibility and the existence of previous relationships, and quality may be related to the competencies of human resources. Issues also have different granularity, with some issues being more general than other (e.g., trust was perceived wider than the existence of a business continuity plan).
6. Discussion
The goals of this study were to identify key issues leading to a successful ISS outsourcing relationship from the point of view of the provider and rank these issues according to their perceived importance.
The first goal–obtaining a list of the most relevant issues–was pursued mainly in the first round of the Delphi study and then refined over subsequent rounds. The blank sheet first round supplied the study with 25 issues (cf. Table 2) that were then trimmed to 13 leading up to the fourth round, and following the stated preferences of the participants (cf. Table 3).
The study accomplished the first goal satisfactorily. This is due to issues spanning a variety of subjects and also because they can be related to issues mentioned in the literature review on ISS outsourcing.
In Table 2 we classified the 25 consolidated issues into five groups. The classification resorted to a subset of categories advanced by Dibbern et al. [2004], only this time used from the providers’ angle.
Part of these issues has been mentioned in the literature review and were known as relevant to the ISS outsourcing relationship. It should however be noted that the existing literature focuses on the client side while this study focuses on the service provider side, thence it is possible to reason that several issues appear to be common to both sides of the outsourcing relationship. Nevertheless, there are issues that seem specific to how service providers perceive the pursuit of a successful ISS outsourcing relationship with the client (security services diversity offered, support in regulatory and legal compliance, existence of a business continuity plan, and decreased operational costs for the provider).
Two criticisms arise though: the first deals with the fact that, even after being stressed constantly throughout the study that the intended point of view was the service providers’, it became obvious in the interviews that some participants always default (maybe unknowingly) to the client’s point of view. To them it is mainly a question of what the client is looking for in a service provider and what can they do to turn the decision in their favour. To a certain extent this makes sense, since the providers’ first goal is to stay in business and therefore have to think like the client in order to position themselves in the market. On the other hand, it makes it more difficult to understand which issues are specific to the provider. The second criticism deals with the fact that the issues have different granularity and they are not completely independent from each other, triggering the participants to easily relate their most important issues to the panel’s most important issues.
The second goal of this study was to rank the issues according to the relevance perceived by the group of participants. The results were not satisfactory. Kendall’s W receded round after round, even when fewer issues were being considered, showing a weak agreement between participants.
The analysis of the convergence effort done by participants over the rounds showed that only 39% of the 104 issues that were ranked over the three rounds (considering the eight participants that answered all ranking rounds and the final thirteen issues) convey a consistent effort by participants to align with the panel’s answer. This means that the convergence effort as a whole was not significant throughout the study. Also, volatility is an issue for several participants. This could be explained by the convergence effort of each participant, trying to move towards the group’s answer. Since the convergence effort was deemed not significant, other reasons have to come into play, such as the degree of robustness of participants’ opinions or shifts on successive answers by participants if they are not aware of their previous answers when they rank issues.
Regarding an overall similar answering behaviour by experts, there is a mild trend, which could be explained by the fact that, round after round, the number of issues is being reduced which inevitably leads to putting the surviving issues in the first positions. Another mild trend noticed is the match of participants’ answers to the group’s, but when the latter changes an overshoot effect seems to arise on the part of the participants.
We think that there is no clear and final reason to why agreement between experts was weak. Volatility of the participants answers, usability of the Web tool used to administer the questionnaires, similarity or dependence between issues, time taken to complete the four rounds of the questionnaires can all be waved but all without proof.
7. Conclusion
This is an exploratory study since no information relating to the service providers’ point of view in ISS outsourcing was found in the literature review and so this study treads new ground. This is increasingly important as outsourcing relationships become more common and tend to become more balanced and regarded as partnerships by the entities involved.
In spite dwelling on a difficult subject, the study was successful. The argument for it being difficult comes from the fact that it is a largely unexplored domain in which there is no background to provide structure to ensuing works, and also because in the field of ISS it is typically hard to harvest information and practitioners tend to not be as forthcoming as they could be.
However, the list of issues here compiled can certainly be a starting point to further studies dwelling on this topic. It can be presented to experts in a Delphi first round, so they can agree or disagree with them, refine and resolve possible inconsistencies and interdependencies between them.
It would also be interesting to assess the clients’ response to this list. Whether they agree or disagree and whether there is any issue which stems any kind of discussion leading to a deeper understanding of the ISS outsourcing relationship.
Several issues have surfaced in the course of this study that may constitute additional work proposals to researchers intending to pursue the topic of ISS outsourcing.
It would be worth to inquire deeper into the aspects that are paramount in winning the client and on the aspects that are paramount in retaining the client. This would help to better understand which aspects are relevant in setting the ISS outsourcing relationship and then in maintaining it.
A second issue is the maturity level of organizations and how it conditions the success of outsourcing relationships at large and ISS outsourcing relationships in particular. Can an organization that does not know itself well be successful in outsourcing any IS function? A related idea would be to study to which extent is the price the dominant factor in resorting to ISS outsourcing and how this relates to the maturity of the organization and its dependence on IS.
Another issue that emerged from this study is about the ISS outsourcing contract. Which is the current state of these contracts and are they generic or specific, helpful or not, and are they effective management tools, litigation instruments or are just ignored?
Lastly, the granularity and overlapping of key issues was a topic of debate during the interviews. Would it be possible to develop a set of key issues balanced in their intrinsic dimension and independent so that a provisional deductive-nomological model may be developed?
These are questions worth pursuing so that we can better understand the perspectives of both parties involved in an ISS outsourcing relationship and to improve the chances of it being successful.
References
Allen, J., D. Gabbard and C. May (2003). Outsourcing Managed Security Services. Software Engineering Institute, Carnegie Mellon University, Pittsburgh.
Alner, M. (2001). The Effects of Outsourcing on Information Security. Information Systems Security 10(2), 1–9.
Brancheau, J., B. Janz and J. Wetherbe (1996). Key Issues in Information Systems Management: 1994-95 SIM Delphi Results. MIS Quarterly 20(2), 225–242.
Brancheau, J. and J. Wetherbe (1987). Key Issues in Information Systems Management. MIS Quarterly 11(1), 23–45.
Dibbern, J., T. Goles, R. Hirschheim and B. Jayatilaka (2004). Information Systems Outsourcing: A Survey and Analysis of the Literature. The DATA BASE for Advances in Information Systems 35(4), 6–102.
Endorf, C. (2004). Outsourcing Security: The Need, the Risks, the Providers, and the Process. Information Systems Security 12(6), 17–23.
Fenn, C., R. Shooter and K. Allan. (2002). IT Security Outsourcing: how safe is your IT security? Computer Law & Security Report 18(2), 109–111.
Gonzalez, R., J. Gasco and J. Llopis (2006). Information systems outsourcing: A literature analysis. Information & Management 43(7), 821–834.
Karyda, M., E. Mitrou and G. Quirchmayr (2006). A framework for outsourcing IS/IT security services. Information Management and Computer Security 14(5), 402–415.
Kern, T. and L. Willcocks (2001). The Relationship Advantage: Information Technologies, Sourcing, and Management. Oxford: Oxford University Press.
Lacity, M. C., S. A. Khan and L. P. Willcocks (2009). A review of the IT outsourcing literature: Insights for practice. Journal of Strategic Information Systems 18(3), 130–146.
Linstone, H. and M. Turoff (1975). The Delphi Method: Techniques and Applications. London: Addison-Wesley.
Okoli, C. and S. Pawlowski (2004). The Delphi method as a research tool: an example, design considerations and applications. Information & Management 42(1), 15–29.
Power, R. and D. Forte (2005). Outsourced or outsmarted? Part II: security outsourcing issues. Computer Fraud & Security 12, 17–20.
Rowe, B., (2007). Will Outsourcing IT Security Lead to a Higher Social Level of Security? WEIS 2007—Workshop on the Economics of Information Security. Pittsburgh.
Schmidt, R. (1997). Managing Delphi surveys using nonparametric statistical techniques. Decision Sciences 28(3), 763–774.
Schneier, B. (2002). The case for outsourcing security. Computer 35(4), 20–26.
Tsohou, A., M. Theoharidou, S. Kokolakis and D. Gritzalis (2007). Addressing cultural dissimilarity in the Information Security Management Outsourcing relationship. Trust, Privacy and Security in Digital Business, LNCS 4657, 24–33. Springer.